Cyberattack – avoid becoming a statistic
Have you experienced this? A critical client e-mail was en route and smartphones weren’t available to me. “You’re welcome to use our courtesy computer,” replied the cheerful attendant. Relieved, I sat down and booted up the available PC.
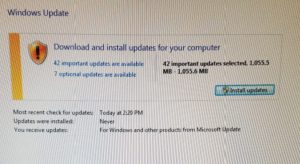 First warning flag: no anti-virus software. Second warning flag: PC was running Windows 7 after January 14 (the date security support was cut off by Microsoft).
First warning flag: no anti-virus software. Second warning flag: PC was running Windows 7 after January 14 (the date security support was cut off by Microsoft).
So, before I was going to log-in to my secure e-mail server, I thought I’d at least better check when the last time the PC had been updated with security batches. The answer? NEVER. When I first logged in, I ironically saw where numerous law firm partners had recently used this same PC to log into their e-mail systems. Now I saw where this particular PC Windows 7 version had 42 critical updates waiting, totaling well over a full gigabit of uninstalled security patches.
It didn’t happen, but I wouldn’t have been surprised to suddenly see the WannaCry ransomware logo scroll across the screen.
What’s the threat all about?
How important is this cybersecurity business? In 2019, more than four billion data records were exposed. (Was your email one of them? Check https://haveibeenpwned.com/). According to a recent IBM report, the average cost of a data breach is $3.9 million, with healthcare getting hit harder at $6.45 million. A little over 25,000 records get exposed per data breach.
Concern over cyberattacks is not limited to large enterprises or institutions. Statistically, one in five (20%) of small businesses can fall prey to a cyberattack. When one hits, about 60% of those business hit typically go out of business with six months.
In addition to IT professionals, more company executives and business owners have awoken to this growing threat. They get it that real cybersecurity goes far beyond simply installing anti-virus programs on PCs and MACs (or smartphones and tablets).
What’s on deck?
Unfortunately, cybercriminals have built ransomware into a business model. As such, according to the cyberservices company BlueVoyant, cyberattackers now have embraced traditional strategic management tools like targeting specific companies (who can pay higher ransoms). Sophisticated cybercriminals now scour social media sites like LinkedIn to scrub freely available personal data to aid in identifying and penetrating victims. Non-segregated backup systems, once touted as the last line of defense in a ransomware attack, now stand exposed as fresh and inviting targets for more sophisticated attacks.
Phishing attacks – where malware-laden emails and web landing pages are carefully built to closely resemble legitimate corporate communication – have also become a new business model for cybercriminals: Phishing-as-a-Service (PhaaS). Low-cost phishing kits and “how-to” advice has become readily available. DNS hijacking, where control of domain registrars and managed DNS providers is breached, represents a new and often effective large scale cyberattack, where bogus DNS info redirects unsuspecting website visitors to clone servers, where sophisticated look-alike web pages readily harvest credit care and other personal data.
The weakest point
CIOs and IT professionals can respond quickly and strategically, but a seriously weak point remains: humans (including employees, vendors and customers) using the internet.
Here’s an example: a company or organization can spend multiple thousands of dollars building sophisticated defense systems against cyberattack. But all preparations can be undone or fatally compromised by a single employee clicking on a link inside an email that looks like it came from the CEO. The click goes to a landing page that looks just like a company landing page, and when prompted to “validate” their response, the employee dutifully enters critical confidential data.
And quietly, with no fanfare or warning, a full-scale breach gets underway.
The point? A critical element of preparing for and preventing a cyberattack must include people using the network. Company data is the lifeblood for continued operations. It must be safeguarded in what has become a decidedly hostile environment.
Like all crises, cyberattacks have both external and internal considerations. Your company probably already has some form of technical preparation in place to limit the scope and impact of a cyberattack. (Has your corporate network been audited for breach potentials?) Hopefully your CEO, legal team and PR/communication staff already have an external cyber crisis plan in place. And if not, consider the $148 million cyber-dumpster fire that internet-dependent Uber ignited when it totally fumbled a response to a 2016 cyber breach; healthcare company Anthem ponied up more than $115 million for a breach that exposed 78 million customers – including the author. (Shameless pitch: don’t have a crisis plan in place, contact MEK to remedy!)
Want to avoid internal issues? Consider these points:
1) Make it known that every employee holds solemn responsibility for cybersecurity and for safeguarding online data. That means using appropriate passwords and not sharing them (or listing them on a post-it note on the PC monitor!).
2) Develop a formal cyber-security policy. Give it teeth. Prohibit visits to websites that are known harbors of malware (usually websites with non-business content that is already prohibited on company computers); start cybersecurity education with the employee on-boarding process. Develop a “Bring-your-own-device” policy – if consulting or other employees bring their own PCs or MACs and use them on a company network, set uncompromising standards for security.
3) Education, education, education. Help employees recognize the seriousness of cybersecurity. Help make employees aware of phishing issues through continuous education. Alert them to avoid pop-ups, unknown e-mails and links that aren’t trusted.
4) Remind them to apply security updates and patches as soon as reasonable (immediately if required). Remind them to update their home devices as well. Limit (or as necessary, prohibit) the portability and use of thumb drives and other portable media that an employee may carry in and infect a corporate computer with.
5) Conduct “live-fire” exercises. Have your IT department or an outside consultant set-up a phishing exercise and see how many employees fall into the cyber net. That response can be a corporate life-saving measure.
6) Don’t forget vendor security. More than one major data breach came in through a breached vendor, where hackers penetrated an otherwise bullet-proof corporate system by entering through less-secure vendor portals.
7) Unfortunately, politeness is not a virtue in corporate espionage. Cybercriminals can gain access to secure physical facilities by faking a stumble right in front of a secured entryway. Polite employees often stop to “help” the cybercriminal up, “gather” the dropped items, and then hold the secure door open for the grateful cybercriminal to walk in. Once in, the cybercriminal finds a deserted office with an Ethernet receptacle, and then…
When it comes to cybersecurity, planned and effective internal communication can literally save a company. Cybersecurity attacks are only going to continue and become more sophisticated, so prepare now.
Michael Snyder, managing principal of MEK, is professionally certified in crisis communications (achieved while working in the Los Angeles market). He has successfully counseled numerous clients, companies and organizations on how to prepare for and survive a crisis (including providing advice as an academic serving on the faculty of Pepperdine and other universities).
